Frequently asked questions about SecuMail Encryption and their answers

General information about encryption
Email encryption | certificate types | about SecuMail EncryptionFunctionality: The content of the email is secured by asymmetric encryption. Both recipient and sender must have an asymmetrical key pair and the corresponding software.
- Encryption:
The sender encrypts the content of the mail with the recipient’s public key, which he knows. The recipient needs his own private key to decrypt the mail. - Lettering:
Outgoing emails are also provided with a signature, which the recipient can use to validate that the email actually comes from the sender and that the content is unchanged. This validation on the part of the recipient is possible with any mail program, even if there is no separate S/MIME key
You can communicate encrypted with all business partners and customers who themselves have a valid S/MIME key and use the corresponding software. This is increasingly the case in the business-to-business environment. Private email addresses, on the other hand, are hardly equipped with S/MIME.
For important mail partners without their own S/MIME, SecuMail Encryption provides Web Encryption (Gina). In this procedure, encryption is provided on the recipient’s side by secure webmail access.
Every S/MIME-signed email you receive from your email partners contains the sender’s public key. This key is extracted and stored during processing so that your reply to the email is automatically encrypted for this key.
The collection of public keys and the decision as to whether an email can be encrypted are handled automatically. Encryption is applied as soon as technically possible. Neither users nor administrators need to intervene.
In the case of domain certificates, a manual entry of all domain certificates in the direction of which encryption is to be carried out is necessary anyway. Mails to domains whose domain certificate SecuMail is known are also automatically encrypted. By the way, this also applies to users who have neither an individual certificate nor a domain certificate.
SecuMail Encryption handles the annual key rollover fully automatically.
One week before a key expires, a new one is generated, which is immediately used for S/MIME signatures in outgoing emails. This allows other systems to learn the new key, while the old key remains available for another week to decrypt emails.
Neither users nor administrators need to take any action.
SecuMail Encryption uses S/MIME certificates from (currently) SwissSign. The certificates are issued securely and fully automatically via the MPKI interface. New certificates can be issued in real time with a click of the mouse, but would be generated automatically at the latest when a registered user sends their first outgoing email.
In order for automatic key generation on behalf of SwissSign to work, your domain must be validated by us during setup. To do this, we require a one-time signature and a TXT entry in the DNS of the mail domain. The DNS entry is renewed annually.
If you want to sign or encrypt emails, you need cryptographic keys. Usually, a key is generated and managed for each person (email address) (individual certificate). However, there is also the option of using a single key for all users (domain certificate).
Difference between single and domain certificates:
- Individual/user certificate: Can sign and encrypt. Everything runs fully automatically (with SecuMail Encryption).
- Domain certificate: manual key management for your own and partner domains, no signatures possible, only one key per email domain instead of per user.
You can find a comparison of the two variants in our SecuMail blog: Learn more
S/MIME technology is well established in the business environment, and it can be assumed that most companies now have at least some addresses or users equipped with S/MIME.
In contrast, private users are rarely equipped with S/MIME due to the considerable IT effort involved for non-experts.
Web encryption enables encrypted communication, even with recipients who do not have S/MIME themselves. To do this, the email is intercepted by the gateway and made available to the recipient as an HTTPS download. The external recipient receives a permanent login to the web gateway and can then view and process encrypted email traffic via their web browser.
Daily use of SecuMail® (for users)
Encrypt emails | Sign emails | Prevent encryptionNo action necessary. Signierung aller ausgehenden Mails und Verschlüsselung wenn der Empfänger als S/MIME-User bekannt ist, funktionieren vollautomatisch. Sie als Benutzer müssen folglich keine manuellen Einstellungen vornehmen.
Ihr Administrator muss keine Anpassungen an Ihrem Mail-Client oder Server vornehmen.
All outgoing mails of the configured users are encrypted as soon as a valid S/MIME certificate of the recipient is known. This applies equally to individual and domain certificates.
All outgoing mails from users who are equipped with a single certificate are automatically signed for all destination addresses without any further settings. The receiver does not have to have its own S/MIME installation. Any mail client can resolve S/MIME signatures.
No action necessary.
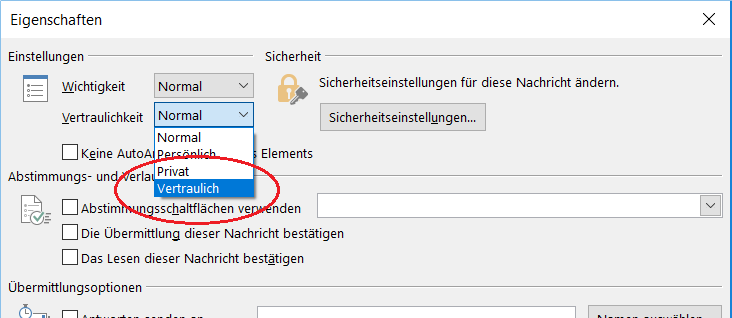
Enforce mail encryption for individual outgoing mails:
- Outlook: Set the “Confidential” flag
OR
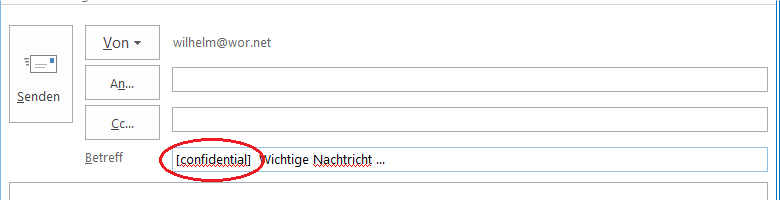
- Write the subject tag “[confidential]” in the subject of the outgoing mail
Permanently enforce mail encryption for individual outgoing mails:
- via a corresponding Outlook plugin
OR
- Enforce encryption for individual addresses or domains permanently using administrator rules. Please contact support for assistance in that case.
You can use the following:
- Install the SeppMail Outlook extension (https://seppmail.de/downloads/) and then deactivate the Encryption button
- Subject Tag: [noenc] prevents encryption, allows signing
- Subject-Tag: [plain] delivers the mail completely unchanged.
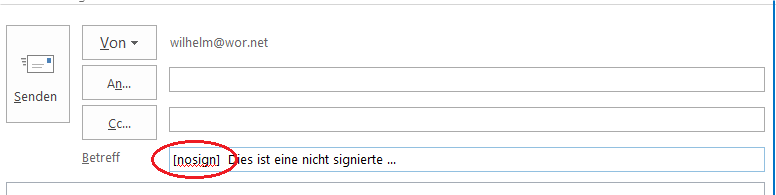
Set the subject tag “[nosign]”:
- When the gateway decrypts an encrypted mail, the [secure] tag is written in the subject
- Emails that have been encrypted incorrectly and therefore cannot be decrypted are returned to the sender as undeliverable.
- Common mail clients validate mail signatures themselves and display this graphically. The signature is checked by the gateway and forwarded unchanged in all cases.
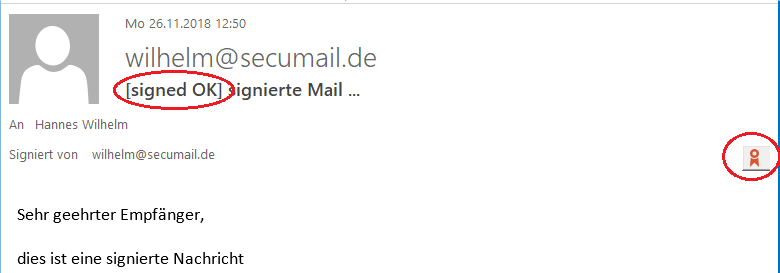
- “[signed OK]” in the subject line: SecuMail Encryption has successfully verified the signature.
Setup and configuration (for IT)
Procedure | Handling | SafetyYes, SecuMail Encryption works with all mail clients and all mail servers. Because it’s a gateway service, you can add S/MIME to your organization in no time and without any technical changes to your infrastructure.
The SecuMail team will be happy to assist and support you in setting up SecuMail Encryption and will provide you with all the necessary information.
Both incoming and outgoing emails are routed via SecuMail:
- incoming emails via MX in DNS
- outgoing mails via the setting for send connector alias relayhost alias smarthost on your mail server to enc.secumail.de
Yes! No changes to your company’s IT infrastructure, processes, or habits are necessary. The technical conversion itself can be implemented simply by adjusting the mail routing.
Users participating in S/MIME or web encryption must be created on the gateway. Not all users of an email domain or company need to participate. Non-participating users/email addresses are routed unchanged and do not incur any costs. However, at least 20% of users of a mail domain should participate in S/MIME, otherwise a small relay fee will be charged.
The SecuMail Encryption Gateway operates fully automatically and without interfering with your IT.
In contrast, all processes must be managed in the mail client itself for single-user installations:
- Key Management
- Encryption and decryption
- Encrypted mails in the mail archive
- Encrypted mails in the mail server
- Opening old encrypted emails with the correct old expired keys (keys change annually)
- User training on use in the mail client
- and so on
SecuMail Encryption is maintenance-free and works reliably out-of-the-box without any intervention from the administrator or users during operation.
SecuMail Encryption works with all mail services and clouds that support mail routing customization.
With Office 365, you can work in the traditional way via MX and Sendeconnector. Alternatively, other available SMTP-based interfaces can be used to route incoming and outgoing mail through SecuMail.
For automatic user creation, import via Graph API is possible.
- Changing your mail routing to set up the system.
- The selection of users who are to participate in S/MIME. (Can be automated via import)
All other essential processes, such as encryption and decryption, signing, key generation, key rollover, collection of public keys, etc., are fully automated.
Calendar invitations and notifications, as well as mails generated in the RTF (winmail.dat, are NOT encrypted, as they cannot be reliably decrypted by recipients due to shortcomings of the various standards and would therefore be inoperable.
In principle, yes. In any case, you must ensure that no unauthorized emails impersonate yours and obtain your signature. We can usually find a solution. Please contact our sales or support team for assistance with this matter.
Below you will find instructions on how to route all outgoing emails from a Microsoft 365 account via SecuMail Encryption (as a relay host):
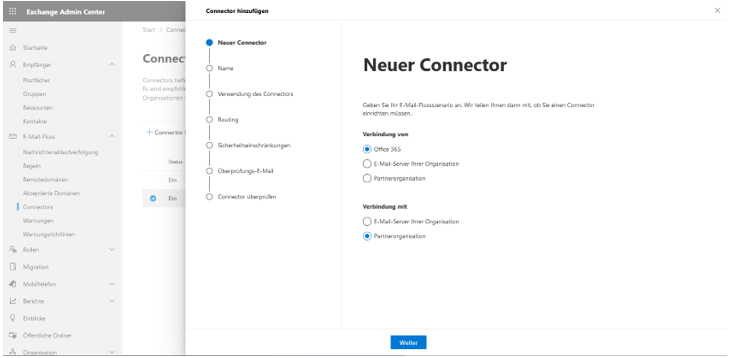
In the Exchange Admin Center, go to “Email Flow” and then “Connectors,” and click the “Add Connector” button to start the wizard for adding a new connector.
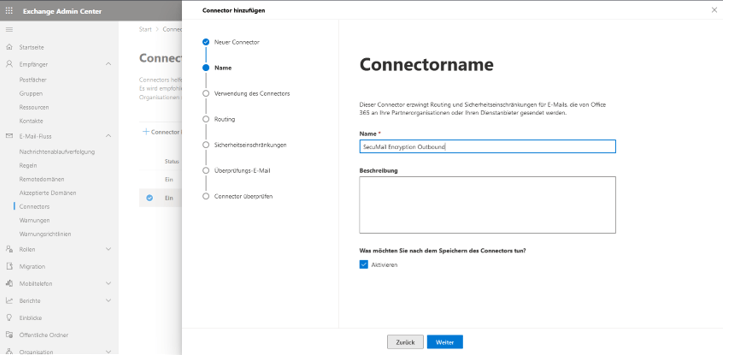
To ensure that the connector can be clearly identified later, it is advisable to use a descriptive name and, if necessary, an additional description.
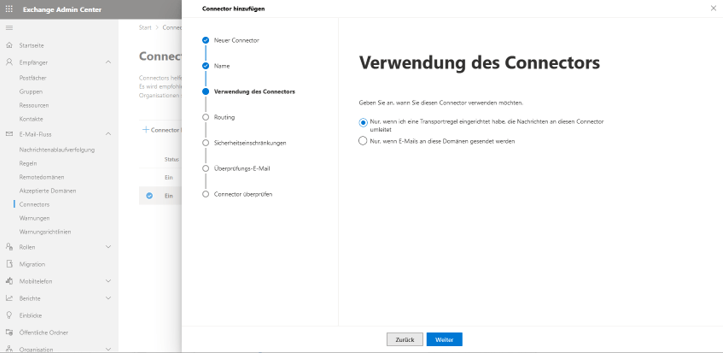
Next, it is specified that the new connector will only be used if a corresponding transport rule applies. The associated transport rule is created in the second part of this guide.
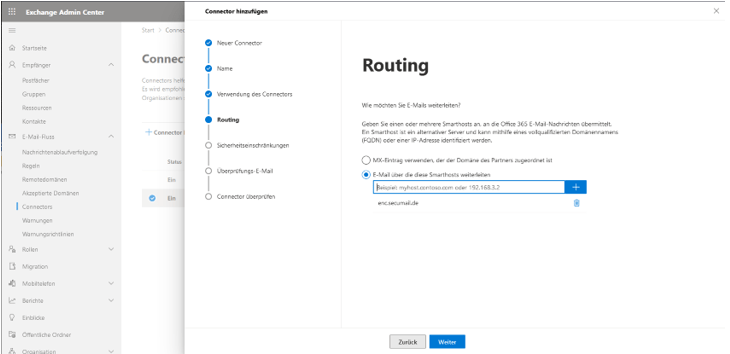
Then you must enter the destination mail server (relay) to which Microsoft 365 or Exchange Online should forward outgoing emails. The server enc.secumail.de must be entered here.
To ensure that emails are transferred between O365 and SecuMail using secure transport encryption, the next step is to check the box next to “Always use TLS.”
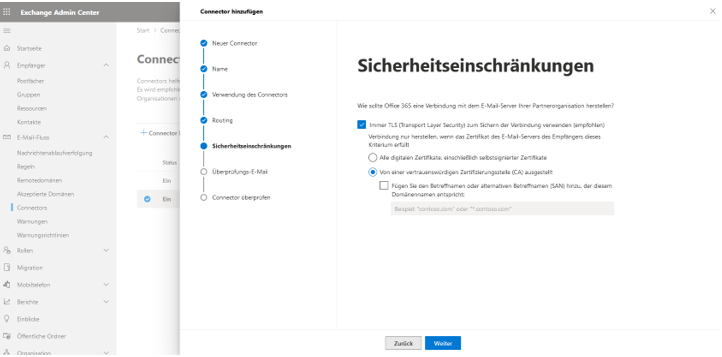
In the final step, the connector’s functionality must be verified with a test email. For example, noreply@secumail.de can be used as the recipient address.
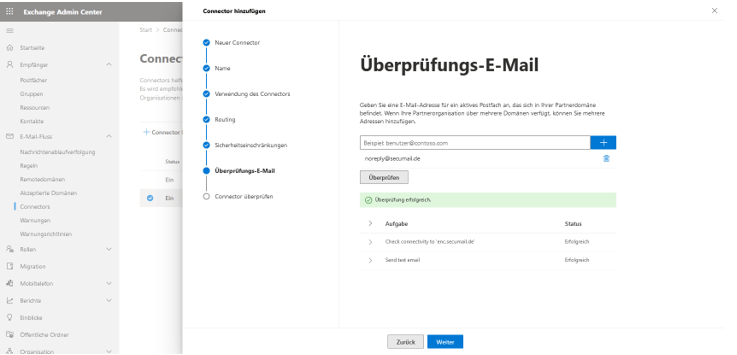
Finally, you will see an overview of the settings you have made and can exit the wizard by clicking “Create connector.”
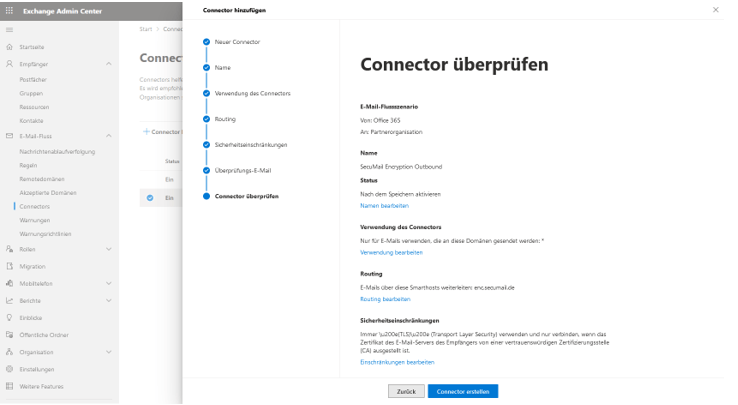
To ensure that the previously created outbound connector is used, a suitable transport rule must then be created. This is done via the menu under “Email Flow” in “Rules.” A new transport rule is now created there using the “Add a rule” button.
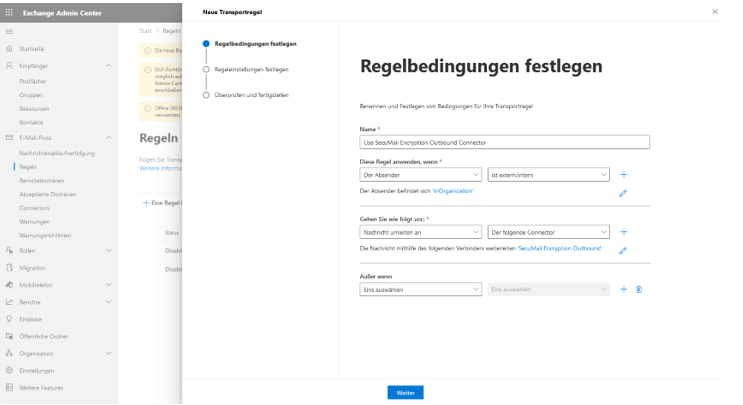
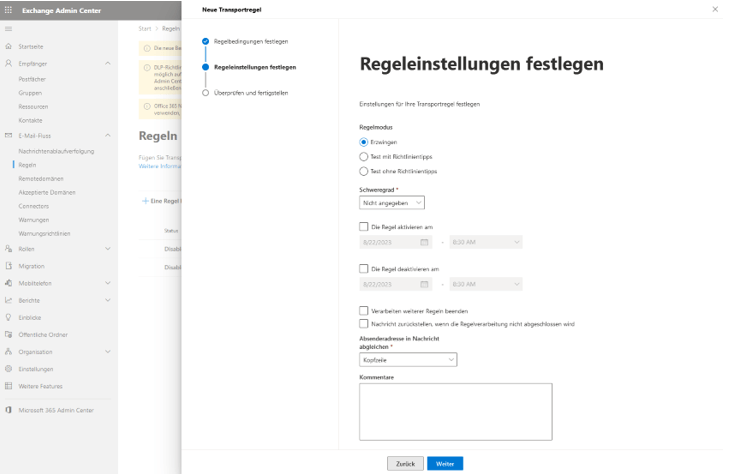
In a standard setup, we recommend the following settings:
- Apply this rule when: The sender is external/internal. The sender is located “InOrganization”.
- Proceed as follows: Forward message to the following connector. Forward the message using the following connector: SecuMail Encryption Outbound.
No special settings are required in the next step. You can simply skip this step by clicking “Next.”
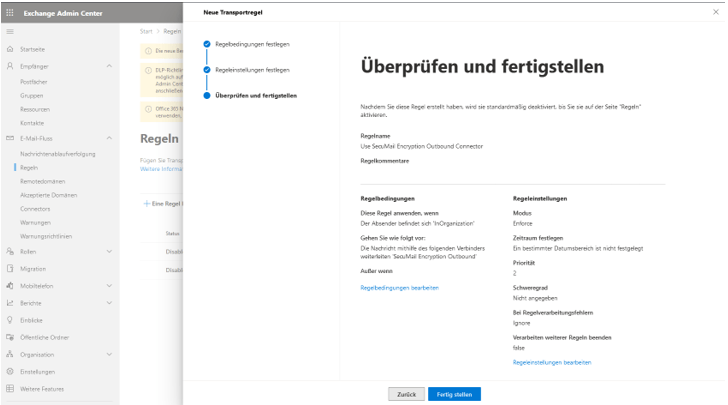
Finally, you get an overview of the new transport rule and can create it by clicking on “Finish”.
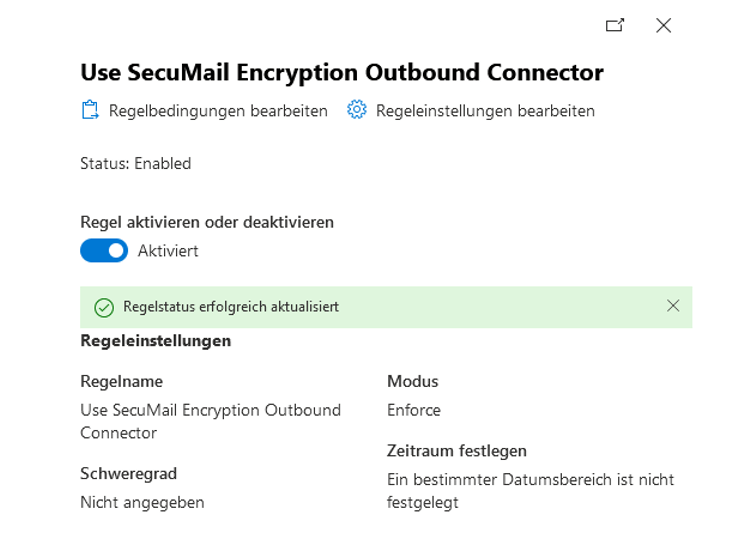
As a final step, the new transport rule must be activated.
If the S/MIME signatures of your outgoing emails cannot be validated and are classified as “untrustworthy” in email programs, this is often due to the following circumstances:
- The client does not have the current root certificates from the trust centers (currently SwissSign).
This can occur with individual, often outdated end devices.
Solution: Update local root certificates. - Apple mobile devices change the content of certain MIME encodings in such a way that the S/MIME signature no longer matches. This is then displayed as a signature error. This occurs frequently when the sender is an MS Exchange server and the recipient is using an Apple mobile device.
The “quoted-printable” format causes some devices or servers to perform subsequent line folding as a “correction,” which of course breaks the S/MIME signatures.
Solution: The sender of the emails can change their MIME encoding settings from “quoted-printable” to “base64.” Alternatively, they can reduce the line length of “quoted-printable.”
Billing (For Purchasing)
Prices | Automatic billing | QuotationWe charge a monthly flat rate per user participating in S/MIME. The certificate is included. There are no additional costs for volume or mail traffic. A one-time validation fee is charged for domain validation and setting up the MPKI interface to the certification authority.
Of course, we also offer SecuMail Encryption for system houses in the white label version familiar from SecuMail Filter.
Let us perpare you an individual offer or call us and we will be happy to advise you.
The SMIME gateway is also billed dynamically based on current usage. SecuMail counts the number of email users participating in encryption. All other addresses are forwarded without encryption/signing and are not charged. At least 20% of the users of a mail domain must participate in SMIME encryption or, alternatively, a relay fee must be agreed upon. Invoices are dynamically adjusted to current usage. Volume discounts are granted for 100, 200, 400, etc. users.
For the whitelabel product variant for system houses, the total number of users across all clients is used to calculate the volume discounts.
Please ask for details of the simple billing method or request an individual offer .
Of course. Both packages can be activated individually or together to protect your email communications. Find out more at angebot@secumail.de or call 08171-246920!
When setting up SecuMail® Encryption, the paid interface to the certification authority must be set up from the outset, which means we cannot offer you a free trial. Please contact our sales team for more information.