Emotet with new distribution channel
An old acquaintance uses a new method to spread his malware.
SecuMail treats downloads like attachments and protects effectively.
Most dangerous malware of the year now uses download links to spread.
This year, the Emotet malware has massively infected many well-known companies and public institutions and caused considerable damage.
So far, Emotet has spread via Office files in the email attachment. These are increasingly detected by email filters.
To avoid this, the malware now infects its victims via a download link. This has several advantages for the malware makers:
- The malware is not part of the e-mail and therefore more difficult to detect by email filters.
- Once the file is on the PC, only the virus scanner can help. However, they react far too slowly for email campaigns.
Deceptively real
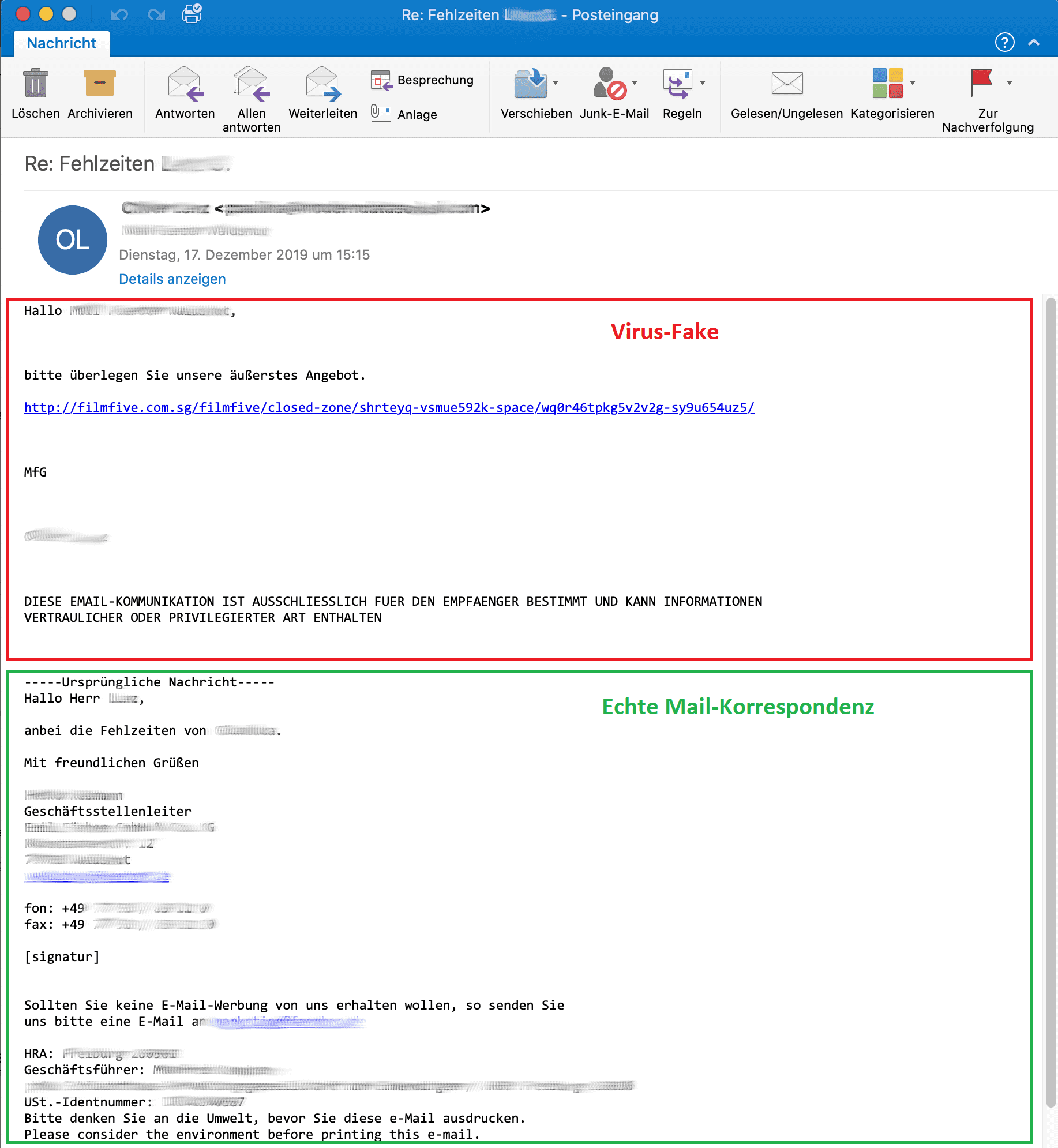
To appear more credible, Emotet uses Outlook harvesting, the evaluation of Outlook data from hijacked computers. If a computer is successfully infected, the address book, email history and signatures are downloaded and used to send deceptively real emails to a new victim.
The malware emails are therefore extremely similar to previous, legitimate emails in terms of content, which increases the likelihood of a fatal mistake – clicking on the download. The example of an Emotet e-mail shown in the image shows a real “hijacked” e-mail correspondence that has been provided with a malicious link.
SecuMail examines downloads
With SecuMail, selected links are examined, downloaded and examined together with the e-mail. This means that the files that are hidden behind links and can therefore be opened with just one click are subject to the same e-mail policy as the attachments. If the download then contains macros or executable code, the entire email will be blocked.
SecuMail has been protecting against this new variant for a long time without having to install an update. In addition, SecuMail generally recommends training employees accordingly (awareness training) in order to further increase security.
Update 20.12.2019: Now also with password-encrypted ZIP archive

We have activated the feature “Prohibit password-encrypted archives” for all customers – even if you had turned it off in the past. The threat level is too high to allow these attachments. The recipients are informed about the withheld mails and can have them forwarded via support – even on holidays.